Android security audit: An 11-step checklist
Android security doesn't have to be a source of stress. These easy-to-follow steps are all you need to keep the boogeyman at bay.

Android security is always a hot topic on these here Nets of Inter — and almost always for the wrong reason.
As we've discussed ad nauseam over the years, most of the missives you read about this-or-that super-scary malware/virus/brain-eating-boogie-monster are overly sensationalized accounts tied to theoretical threats with practically zero chance of actually affecting you in the real world. If you look closely, in fact, you'll start to notice that the vast majority of those stories stem from companies that — gasp! — make their money selling malware protection programs for Android phones. (Pure coincidence, right?)
The reality is that Google has some pretty advanced methods of protection in place for Android, and as long as you take advantage of those and use a little common sense, you'll almost certainly be fine (yes, even when the Play Store guards slip up and let the occasional bad app into the gates). The biggest threat you should be thinking about is your own security surrounding your devices and accounts — and all it takes is a few minutes a year to make sure your setup is sound.
Take the time now to go through these quick 'n' simple steps, and set a reminder to revisit this page in another 12 months. Then rest easy the rest of the year knowing the mean ol' Android malware monster won't be banging down your virtual door anytime soon.
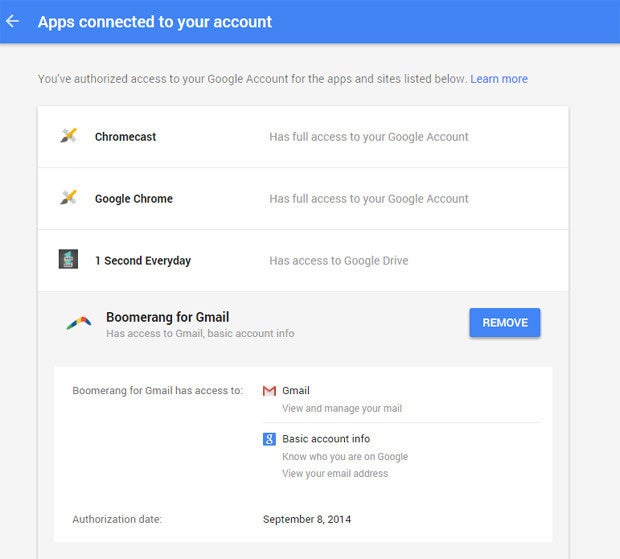
Android security step 1: Look over all the apps and services connected to your account
You've probably granted countless apps access to parts of your Google account over time — which is no big deal in general, but if you're no longer using those apps, it's advisable to close those connections.
Visit this page in Google's security settings to see a list of everything that's authorized and what exactly it can access. If you see anything you don't recognize or that you no longer use, click it and then click the blue "Remove" button to give it the boot.
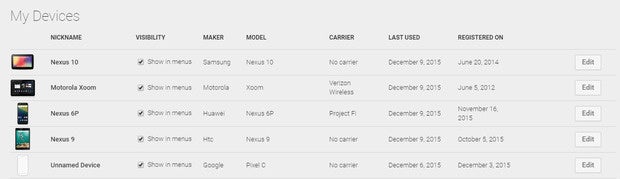
Android security step 2: Clean up your list of connected devices
Anytime you sign into a new device with your Google account — be it an Android phone, a Chromebook, or even just the Chrome browser on a regular PC — that device is added to an approved-for-access list and associated with your account.
Click over to this page in Google's security settings and give your list a once-over. If you see any old devices you no longer use, click on them and then click the bright red button to make sure they no longer have access to your account. And if you see any devices you've never used, remove them right away — and then go change your account passwordimmediately.
Android security step 3: Clean up your devices in the Play Store
This one isn't directly related to security, but it's a good bit of housecleaning to perform while you've got your cleaning hat on: Head over to the Google Play Store settings and look at your list of available devices. These are the Android devices that show up as options every time you install a new app from the Play Store web interface — and also the devices that show up as options in Google's Find My Device utility (more on that in a sec).
Go ahead and uncheck the box next to "Show in menus" for any devicesyou no longer use. And if you see any devices with weird cryptic codenames, click the "Edit" button alongside them and rename them to something you'll recognize.
The next time you download an app or remotely locate one of your devices will be a much smoother experience as a result.
Android security step 4: Make sure Find My Device is activated and ready to go on all your current devices
You might not realize it, but Google has its own utility for tracking, finding, and remotely wiping an Android device in case you ever lose it — and the whole system is built right into the operating system.
So what are you waiting for? Make sure all of your phones and tablets are enrolled now, before it's too late. Just head into the Google section of each device's main settings menu (or look for the app called Google Settings). Tap "Security" and then "Find My Device," and make sure the blue toggle within that section is activated.
You'll also need ensure that location access is enabled on your device — which it probably is, but it's worth double-checking by pulling up the Security & Location section of your system settings and confirming that the toggle within "Location" is activated.
Now bookmark the web version of Find My Device and/or download the app on a Chromebook or any other Android-compatible device you own. If you ever can't find your phone or tablet, open the service, and you'll be able to pinpoint precisely where the missing gadget was last seen. You can also force it to ring, remotely lock it, or — in a worst-case scenario — erase it entirely.
(Bonus tip: You can also always just type "find my device" into the Google search prompt in any browser. Provided you're signed in, that'll pull up a box with location info for any connected devices right then and there, within the search results.)
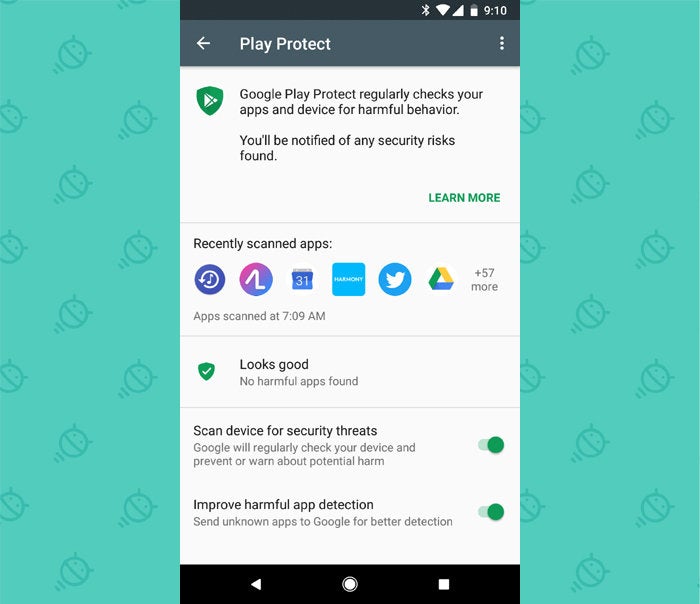
Android security step 5: Verify that you're using Android's app-scanning system
Android has long had the ability to monitor your device for harmful code or suspicious activity — no third-party apps or add-ons required. And while the system should be enabled by default on any reasonably current device, it's a good idea to confirm that everything's turned on and working the way it should.
Mosey on back to the Security & Location section of your system settings (or the Google section of your system settings) and tap the line labeled "Google Play Protect" — then make sure "Scan device for security threats" is checked. That'll allow Android's app verification system to keep an eye on all apps on your device, even after they're installed, and make sure none of them does anything dangerous. The scanning will run silently in the background and won't ever bother you unless something suspicious is found.
Odds are, you'll never even know it's there. But it's a valuable piece of protection and peace of mind to have.
(And remember, too, that this works hand in hand with Android's long-standing systems for scanning newly downloaded applications and checking them for potentially harmful code before they're installed — and for scanning and monitoring all apps uploaded to the Play Store before you ever get to them. There's also a built-in system for detecting SMS abuse and blacklisting sources that have exhibited shifty behavior in the past. All in all, 99.9% of the time, the bases are pretty thoroughly covered.)
Android security step 6: Appraise your app-downloading IQ
If you're reading this column, I probably don't need to tell you this — but I will, anyway: While we're thinking about the subject of Android security, take on a teensy bit of responsibility and commit to letting common sense guide your app-downloading decisions.
Look, let's not kid ourselves: Google's security mechanisms are invariably going to fail on occasion. There's no getting around that. But even when a shady app makes its way into the Play Store, all it takes is the tiniest shred of awareness to avoid having it affect you in any way.
Just as you do when browsing the web from a computer, look at something before you download it. Look at the number of downloads and the overall reviews. Think about what permissions the app wants and whether you're comfortable with the level of access it requires. Click the name of the developer, if you still aren't sure, and see what else they've created. And unless you really know what you're doing, don't download apps from random websites or other unestablished third-party sources. Such apps will still be scanned by Google's on-device security system before they're installed, but your odds of encountering something shady are definitely more significant out in the wild than in the Play Store.
(Your Android device won't let you download apps from unknown sources by default, anyway, so if you ever try — even inadvertently — you'll be warned and prompted to authorize that specific form of non-Play-Store download. Apps on Android will never magically install themselves without your explicit permission.)
By and large, all it takes is a quick 10-second glance to size something up and see if it's worth installing. With all due respect to the dodos of the world, it doesn't take a rocket scientist to stick with reputable-looking apps and avoid questionable creations.
Android security step 7: Double-check your security basics
One more no-brainer that's nevertheless important to mention: If you aren't using biometric security and/or a PIN, pattern, or password on any of your devices, start doing it. Now.
Talk to any security expert, and you'll hear the same thing: The most likely cause of a security failure is simply a failure on your behalf to secure your stuff. You are the weakest link, as the cool kids said 10 to 15 years ago.
Embarrassingly dated pop culture references aside, think about it: If your phone has no passcode protecting it, all of your data is just out there and waiting for the taking anytime you leave the device unattended (intentionally or otherwise). That includes your email, documents, social media accounts, and entire photo collection (yes, even those pictures — hey, I'm not here to judge).
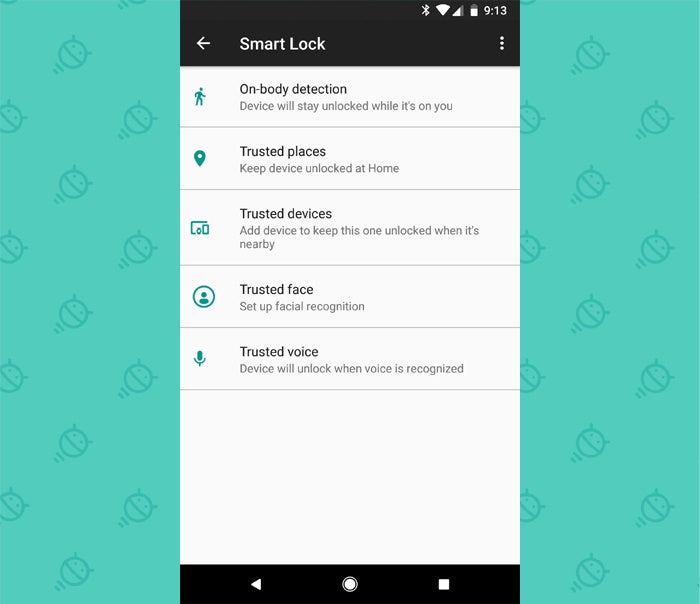
The best part: Android makes it impressively painless to keep your devices secure nowadays. The software's Smart Lock function makes it possible to automatically leave your phone unlocked in a variety of preapproved "safe" conditions — like when you're at home, when a specific trusted Bluetooth device is connected, or even when the phone is being carried in your pocket. That means the extra security shows up only when it's really needed, and you don't have to mess with it the rest of the time.
Plain and simple, there's no excuse to leave your stuff unprotected anymore. Head into the Security & Location section of your device's settings to get started, if you haven't already.
Android security step 8: Peek in on your saved Smart Lock passwords
One of the less frequently discussed parts of Android's Smart Lock system is its ability to save passwords for websites and apps accessed via your mobile devices. As part of your Android security audit, glance over the list of saved passwords Google has for your account so you'll know what's there — and while you're at it, take a few seconds to remove any dated items that are no longer needed and don't belong.
Android security step 9: Evaluate your two-factor authentication situation
A single password isn't enough to protect an important account these days — especially one as wide-reaching and valuable as your Google account. Two-factor authentication makes it so that you have to put in a special time-sensitive code in addition to your password anytime you try to sign in. That significantly increases your level of security and decreases the odds of anyone ever being able to break in and access your personal data, since they'd need both knowledge of your password and the physical presence of your code-generating device (most likely your phone) to do it.
If you don't yet have two-factor authentication enabled for your Google account, head over to this site to get started. Once you have things configured, you'll use an app like Google's own Authenticator to generate single-use codes from your phone or a third-party alternative like Authythat can run on your phone as well as on other devices.
Speaking of Authy, if you're already using that for two-factor authentication, open the app right now and head into the My Account section of its settings, then tap "App Protection" and confirm that you're using a PIN or fingerprint for protection. Then pop over to the Devices section of the same settings menu to check up on exactly what devices are authorized to access the app. Remove any that are dated and no longer in use.
If you really want to keep your account secure, by the way, Google also now offers a souped-up option called Advanced Protection. It requires you to purchase physical security keys and then use those anytime you sign into your Google account. It also severely limits the ways in which third-party apps can connect to your account. This sort of elevated and locked-down setup probably won't be sensible for most typical users, but if you feel like you need the extra protection, you can learn more and enroll here.
Android security step 10: Perform a general Google security check to round things out
Take a deep breath: We're almost done! This next-to-last step will take you through a broad security check that'll look for any remaining weak points in your Google account and Android security and will prompt you to fix them right then and there.
Just go to this Google security site and click through any issues it presents. It'll confirm that you've successfully performed many of the actions we've already discussed and will look for any other potential red flags or opportunities for improvement.
Consider it your confirmation that your personal security setup is A-OK.
Android security step 11: Think carefully about third-party security apps and whether you really need them
Now that you've made sure your Android security situation is shipshape, think about any third-party security tools you're using (whether you installed them or they came preinstalled on your phone or tablet) and what they're actually adding to your device. I'm talking Lookout, Avast, Norton, McAfee, AVG — all those sorts of programs.
You've already verified that your device is protected. Android is actively scanning for threats on several levels, both on the server side at the Play Store and on your phone as new apps arrive (from any source) and continuing over time. Plus, you're exercising basic smarts about what apps you download. The operating system is even looking out for SMS-based scams, and the Chrome for Android browser is keeping an eye out for web-based threats as well.
Beyond all of that, your devices are all enrolled in a sophisticated cross-platform system for remotely tracking, pinging, and erasing as needed. And all of that is happening on the native platform level.
So given those layers, is the third-party security app on your phone doing anything that isn't redundant and unnecessary? It's probably eating up system resources and impacting performance for no real reason — and quite likely also costing you money you don't need to be spending — but is it actually accomplishing anything of value that Android itself isn't already handling in a more direct manner?
The answer is almost certainly no. If having an extra security app makes you feel safer, hey, do what works for you. But if you've completed every step of this audit, there's really no reason you need it — and every reason to send it packing.
And with that, my fellow security-seekers, consider yourself audited. Set your reminder now to revisit these steps this same time next year. The areas we've just discussed are prone to evolve over time, and checking in on them annually is the best way to ensure your virtual house is always in order.
Comments
Post a Comment